Interconnected digital workplace, email and collaboration platforms serve as the backbone of organizational communication. However, these essential channels have become primary attack vectors for cyber criminals seeking to exploit vulnerabilities through phishing campaigns, malware distribution, and data exfiltration. Traditional security measures, while foundational, are increasingly insufficient against sophisticated threats that evolve rapidly and employ advanced evasion techniques. The solution lies in next-generation security platforms that harness artificial intelligence and machine learning to provide comprehensive, real-time protection across all communication channels.
The Evolution of Email and Collaboration Threats
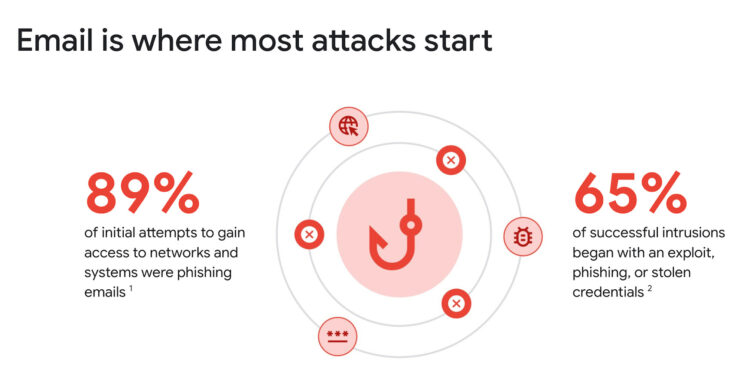
Modern cyber threats have evolved far beyond simple spam filters and basic virus detection. Today’s attackers employ sophisticated social engineering tactics, zero-day exploits, and advanced persistent threats that can bypass conventional security measures. Phishing attacks have become increasingly targeted, with criminals conducting extensive reconnaissance to craft convincing messages that appear to come from trusted sources. These business email compromise attacks often result in significant financial losses, with the FBI reporting billions in annual damages from such schemes.
Collaboration platforms present unique challenges as they facilitate real-time communication, file sharing, and integration with multiple third-party applications. Each integration point represents a potential vulnerability that attackers can exploit. Traditional security approaches that rely on signature-based detection or rule-based filtering struggle to keep pace with the dynamic nature of these threats, particularly when attackers employ machine learning techniques to optimize their campaigns.
AI-Powered Threat Detection: A Paradigm Shift
Artificial intelligence and machine learning technologies have revolutionized email and collaboration security by enabling systems to learn from patterns, adapt to new threats, and make intelligent decisions in real-time. These advanced systems analyze vast amounts of data, including email content, sender behavior, network traffic patterns, and user interactions, to identify potential threats that would otherwise go undetected.
Machine learning algorithms excel at detecting anomalies that indicate malicious activity. For instance, an AI system can identify subtle changes in writing style that suggest an email account has been compromised, or recognize unusual login patterns that indicate unauthorized access. Natural language processing capabilities enable these systems to understand context and intent, allowing them to distinguish between legitimate urgent requests and social engineering attempts.
The power of AI lies in its ability to process and correlate information from multiple sources simultaneously. While a human security analyst might struggle to connect seemingly unrelated events across different platforms, AI systems can instantly identify patterns that span email, cloud storage, messaging applications, and other collaboration tools. This holistic approach provides a more comprehensive security posture than traditional point solutions.
Real-Time Threat Detection and Response
One of the most significant advantages of AI-powered security solutions is their ability to provide real-time threat detection and response. Traditional security measures often rely on periodic scans or batch processing, which can leave organizations vulnerable during the intervals between checks. AI systems continuously monitor communication channels, analyzing each message, file transfer, and user interaction as it occurs.
Real-time detection capabilities enable immediate response to emerging threats. When a suspicious email is detected, the system can automatically quarantine the message, alert security teams, and prevent similar threats from reaching other users. This rapid response capability is crucial in preventing the spread of malware or stopping phishing campaigns before they can cause significant damage.
Advanced AI systems employ predictive analytics to anticipate potential threats before they materialize. By analyzing historical attack patterns, current threat intelligence, and organizational behavior, these systems can identify indicators of compromise that suggest an attack is imminent. This proactive approach allows security teams to strengthen defenses and prepare countermeasures before threats become active.
Comprehensive Platform Protection
Modern organizations rely on diverse collaboration platforms, including cloud-based email services, messaging applications, file-sharing platforms, and video conferencing tools. Each platform presents unique security challenges and attack vectors. AI-powered security solutions address this complexity by providing unified protection across all platforms while adapting to the specific requirements and vulnerabilities of each environment.
Cloud email security leverages AI to analyze email metadata, content, and attachments in real-time. Advanced systems can detect sophisticated phishing attempts that use legitimate-looking domains, identify malicious URLs that redirect through multiple layers of obfuscation, and recognize social engineering tactics that exploit current events or organizational changes. Machine learning algorithms continuously improve their detection capabilities by learning from new attack patterns and false positive feedback.
Collaboration platform security extends beyond email to include messaging applications, file-sharing services, and integrated third-party tools. AI systems monitor these platforms for suspicious activities such as unusual data access patterns, unauthorized file sharing, or anomalous user behavior. The integration of multiple security layers ensures that threats attempting to move laterally across platforms are detected and contained.
Data Loss Prevention and Insider Threat Detection
AI-powered security solutions excel at preventing data loss and detecting insider threats, which are among the most challenging security concerns for organizations. Traditional data loss prevention tools rely on predefined rules and patterns, which can be easily circumvented by determined actors. AI systems, however, can understand context and intent, enabling them to identify potential data exfiltration attempts even when they don’t match specific patterns.
Machine learning algorithms analyze user behavior patterns to establish baselines for normal activity. When users deviate from these patterns, particularly in ways that suggest potential data theft or misuse, the system can flag these activities for investigation. This approach is particularly effective at detecting insider threats, where authorized users may abuse their access privileges to steal sensitive information.
Advanced AI systems can also identify sensitive data that may not be explicitly classified, using content analysis and pattern recognition to detect personally identifiable information, financial data, or intellectual property. This capability ensures comprehensive protection even when data classification processes are incomplete or inconsistent.
Implementation Considerations and Best Practices
Successful implementation of AI-powered email and collaboration security requires careful planning and consideration of organizational needs. Organizations must evaluate their existing security infrastructure, identify gaps in protection, and develop integration strategies that minimize disruption while maximizing security benefits.
Training and user education remain critical components of any security strategy. While AI systems can detect and prevent many threats automatically, users must understand their role in maintaining security. This includes recognizing social engineering attempts, following proper data handling procedures, and reporting suspicious activities promptly.
Continuous monitoring and refinement of AI systems ensure optimal performance over time. Security teams must regularly review detection accuracy, adjust thresholds to minimize false positives, and update threat intelligence feeds to maintain protection against emerging threats. Regular testing and validation of security controls help ensure that AI systems remain effective as threats evolve.
Future of AI-Powered Security
The future of email and collaboration security will likely see even more sophisticated AI implementations, including advanced behavioral analysis, predictive threat modeling, and automated response capabilities. As organizations continue to adopt cloud-based collaboration tools and remote work becomes more prevalent, the need for intelligent, adaptive security solutions will only grow.
AI-powered security represents a fundamental shift from reactive to proactive protection, enabling organizations to stay ahead of evolving threats while maintaining the productivity and collaboration capabilities that drive business success. By leveraging the power of artificial intelligence and machine learning, organizations can create robust security postures that protect against current threats while adapting to future challenges in the ever-evolving cybersecurity landscape.
