Understanding AITM Attacks: Why Token Hardening Matters More Than Ever
Cybersecurity threats are constantly evolving, and one attack method that’s been gaining serious traction lately is the Adversary-in-the-Middle (AITM) attack. If you haven’t heard of these yet, you’re not alone – but you definitely should know about them, especially if you’re responsible for protecting user accounts or sensitive data. What Exactly Are AITM Attacks? Think […]
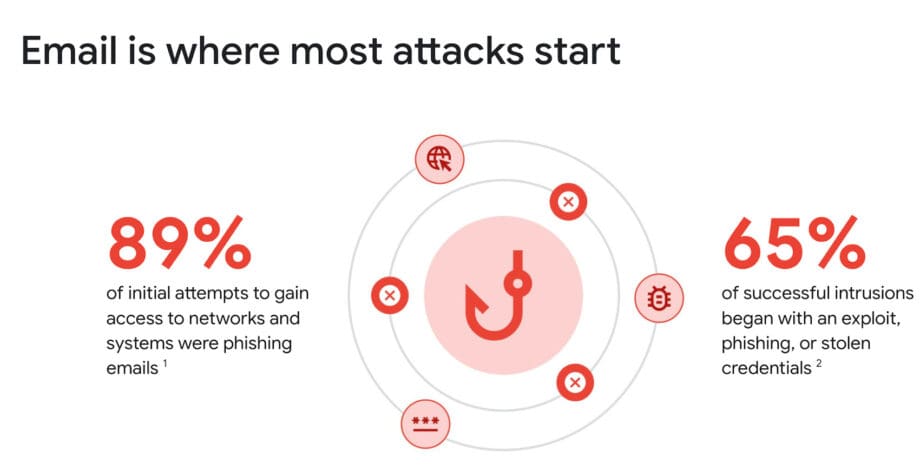
Advanced AI Powered Email Security for Business Communications
Interconnected digital workplace, email and collaboration platforms serve as the backbone of organizational communication. However, these essential channels have become primary attack vectors for cyber criminals seeking to exploit vulnerabilities through phishing campaigns, malware distribution, and data exfiltration. Traditional security measures, while foundational, are increasingly insufficient against sophisticated threats that evolve rapidly and employ advanced […]