Protecting a company’s digital assets with cybersecurity solutions is akin to safeguarding a pod of orca whales swimming in dangerous waters. Just as these majestic creatures navigate treacherous seas, businesses must navigate the complex and ever-evolving landscape of cyber threats. Let’s explore this analogy further by comparing cybersecurity solutions to the security measures employed by orca pods.
Firstly, consider the role of threat intelligence in both scenarios. Just as orcas rely on their acute senses and social networks to detect potential dangers, cybersecurity solutions leverage threat intelligence to identify and assess emerging threats. By analyzing patterns and behaviors, both orcas and cybersecurity solutions can anticipate and respond to threats effectively.
Next, let’s examine the importance of collaboration and communication. Orcas exhibit remarkable teamwork and communication within their pods, allowing them to coordinate hunting strategies and protect one another from predators. Similarly, cybersecurity solutions often involve collaboration between various tools and technologies, such as firewalls, antivirus software, and intrusion detection systems. By working together and sharing information, these solutions can defend against cyber threats more effectively.
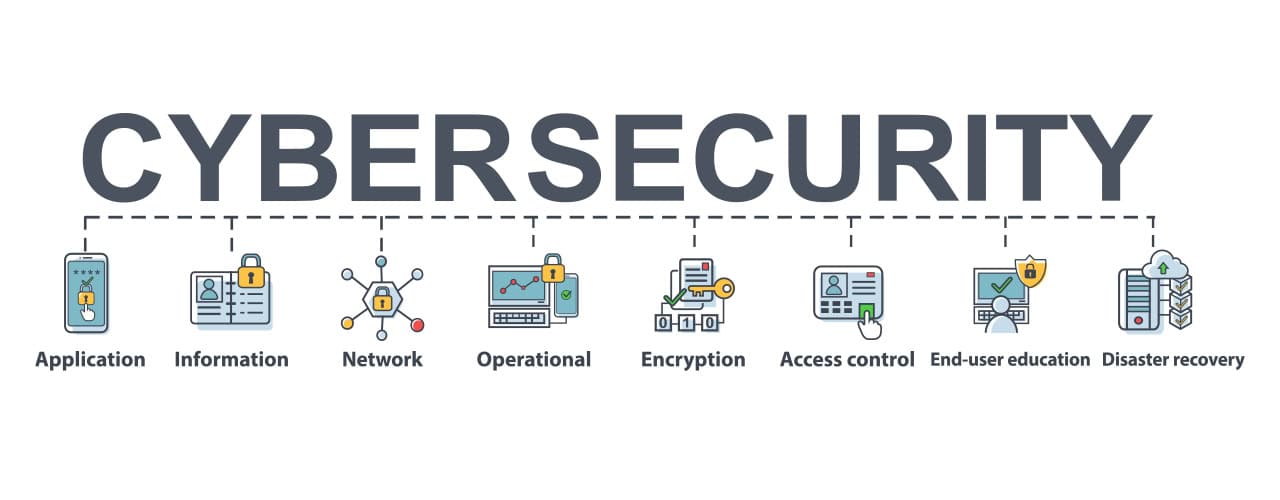
Furthermore, consider the concept of defense in depth. Orcas employ a multi-layered approach to defense, using their size, speed, and intelligence to deter potential threats. Similarly, cybersecurity solutions utilize a defense-in-depth strategy, implementing multiple layers of security controls to protect against different types of cyber attacks. This includes perimeter defenses, endpoint security, network segmentation, and data encryption, among others.
 Moreover, both orcas and cybersecurity solutions must adapt to changing environments and threats. Orcas continuously assess their surroundings and adjust their behavior accordingly, while cybersecurity solutions employ dynamic threat detection and response mechanisms to adapt to evolving cyber threats. This agility is essential for staying ahead of adversaries and maintaining effective security posture.
Moreover, both orcas and cybersecurity solutions must adapt to changing environments and threats. Orcas continuously assess their surroundings and adjust their behavior accordingly, while cybersecurity solutions employ dynamic threat detection and response mechanisms to adapt to evolving cyber threats. This agility is essential for staying ahead of adversaries and maintaining effective security posture.
Finally, consider the importance of resilience and recovery. Despite their formidable defenses, orca pods may still face challenges or setbacks in their environment. Similarly, cybersecurity solutions must be resilient to withstand attacks and recover quickly in the event of a breach. This involves implementing robust incident response plans, data backup strategies, and disaster recovery procedures to minimize the impact of cyber incidents.
In summary, the security of a company’s digital assets with cybersecurity solutions can be compared to the security of a pod of orca whales swimming in dangerous waters. Both scenarios require threat intelligence, collaboration, defense in depth, adaptability, and resilience to protect against potential threats effectively. By adopting similar strategies and principles, businesses can enhance their cybersecurity posture and mitigate the risks posed by cyber threats.
Our Mission
Our mission is to fortify your hybrid environments with robust cyber security solutions, ensuring seamless protection across digital landscapes. We pledge to safeguard data integrity, privacy, and infrastructure, empowering clients to navigate the complexities of modern connectivity with confidence.
Our Vision
In envisioning the future of cyber security in hybrid environments, we aspire to be the trusted guardians of digital assets. Our vision is to pioneer innovative solutions that seamlessly integrate with evolving technologies, safeguarding businesses and individuals against emerging threats with unwavering excellence and integrity.
Researchers from Google said they observed 97 zero-days exploited in the wild in 2023, compared to 62 in 2022 — a 50 percent increase.




